Introduction
This short guide provides details on how to configure Beyond Identity as an Identity Provider in the Curity Identity Server.
Prerequisites
-
An installation of the Curity Identity Server. A good starting point is to follow the Getting Started Guide.
-
Access to a Beyond Identity Tenant and an OIDC client configured. Make sure to note the
Client ID&Client Secret. Request a tenant here if you do not already have access. -
An installation of the Beyond Identity Platform Authenticator.
Configuration
Beyond Identity
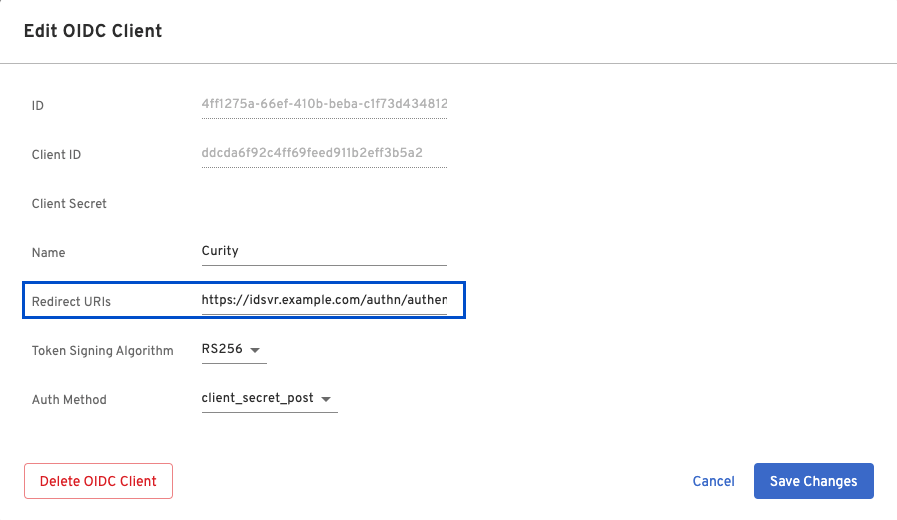
Outside of the prerequisites the only configuration that is needed on the Beyond Identity side is to make sure that an appropriate redirect_uri is configured in the OIDC client that is going to be used. Example: https://idsvr.example.com/authn/authentication/beyond/callback.
https://idsvr.example.comis the baseURL configured in the Curity Identity Server/authn/authenticationis the default authentication endpoint/beyondis the ID of the OpenID Authenticator configured in the Curity Identity Server/callbackis indicating that this is the callback where the Beyond Identity Platform Authenticator should redirect back to when user authentication is completed
The Curity Identity Server
If the Getting Started Guide is followed an OAuth client should have been configured. A new Authenticator needs to be configured.
- Navigate to
Profiles->Authentication Service->Authenticators-> ChooseNew Authenticator - Give it a name (
beyondin this documentation) and chooseOIDCas the type, click Next - Add the Configuration URL -
https://auth.byndid.com/v2/.well-known/openid-configuration - Add the
Client IDobtained from the Beyond Identity Admin UI - Add the
Client Secretobtained from the Beyond Identity Admin UI - Set
Client Authentication Methodto client-secret - Enable
Use HTTP Basic Authentication
Test using OAuth.tools
Assign the new authenticator to an OAuth client that has the Code Flow enabled in the Curity Identity Server.
Using that client in OAuth.tools , initiate a Code Flow. If multiple authenticators are configured for the client select the previously created OIDC Authenticator (beyond).
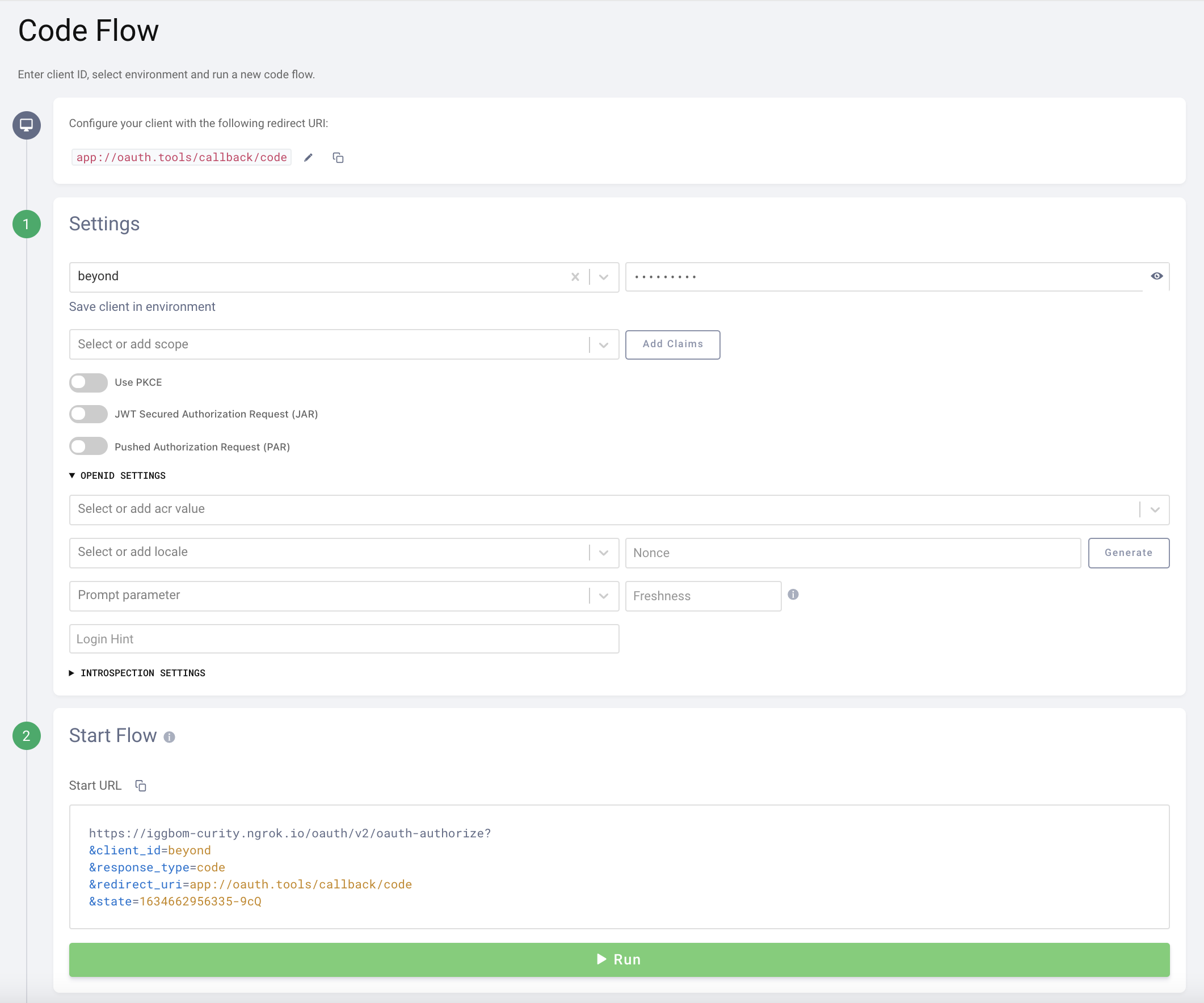
The flow should automatically trigger the Beyond Identity Platform Authenticator, authenticate the user and then direct back to OAuth.tools. If Auto-redeem code is enabled an Access Token, Refresh Token and optionally an ID Token should be issued.