Admin Console actions to support the various development options
Admin Console
In the Admin Console, there are a number of options for token configuration within your application.
Note: Refresh tokens can only be configured and enabled for applications with an "Authorization Code" grant type.
- Client Credentials
- Authorization Code



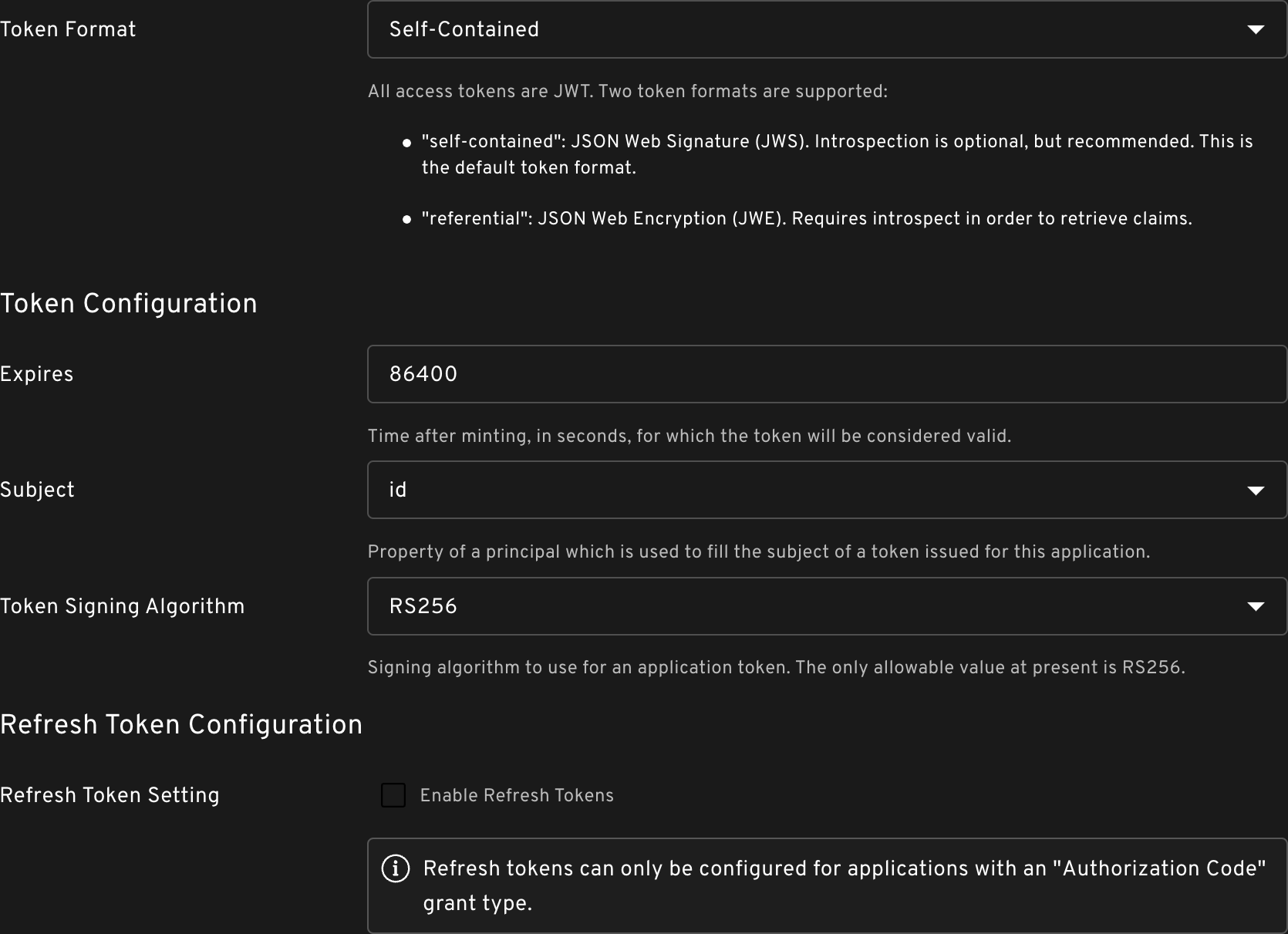
Token Format
There are two token formats that can be validated: self_contained or referential.
The main distinguishing factor is whether introspection is optional or required. Self-contained tokens contain claims which can be used to validate the token. Referential tokens require an introspect call in order to retrieve the claims and validate the token.
When validating self-contained tokens, consider if you want to revoke your tokens. If revoked tokens are accepted (as in a MVP case), then the token can be validated offline by validating the signature and parsing the claims of the JWT token. In all other cases the token should be introspected.
Token Configuration: Expires
This is the time, in seconds, for which the token will be considered valid after minting. The default value is 86400, or 24 hours.
Token Configuration: Subject
Property of a principal which is used to fill the subject of a token issued for this application. The default value is id. You may also choose to use email or username. In case of applications with client_credentials grant type, the only valid value is id because there is no email nor username available in an application.
Token Configuration: Token Signing Algorithm
The Token Signing Algorithm is is the algorithm to used to sign a token. The only allowable value at present is RS256. RS256 algorithm is an asymmetric algorithm that uses a private key to sign a JWT and a public key to verify that signature.
Refresh Token Configuration: Refresh Token Setting
The Refresh Token Setting allows you to enable refresh tokens. The default is disabled.
If enabled, when an access token is minted, a refresh token will also be minted. When an access token expires, the refresh token can be used to exchange for a new access token, via the token endpoint as described in RFC-6749#6.
If disabled, when an access token is minted, a refresh token will not be minted. When an access token expires, the user will need to authenticate, and a new access token can be minted.
Refresh Token Configuration: Absolute Duration
The Absolute Duration is the total amount of time, in seconds, a refresh token is allowed to live before a user must re-authenticate. The default value is 0, which means that the token expires immediately.
When a refresh token expires, the user will need to authenticate, and a new access token and refresh token pair can be minted.
Refresh Token Configuration: Rotate
Rotate defines if the server should issue a new refresh token on each call to the refresh_token flow, or if the client could hold onto the old token. True if rotation should be enabled. The default is disabled.
If rotation is enabled, then the old refresh tokens are revoked each time a new refresh token is minted, and must be discarded.
If rotation is disabled, then a refresh tokens may continue to be used until it expires or is revoked.